WhatsApp was previously great for privacy, using end-to-end encryption to keep messages secure. However now I am regretful that WhatsApp has changed its privacy settings to share user data with parent company, Facebook. Now the encryption remains, but rumors are that WhatsApp may share phone numbers, user names, contact details locations and much more - I must ask why they even bother with the encryption?! The content of your messages may stay secure but your identity might not!
#WhatsAppPrivacyPolicy has been trending on twitter because of these changes, with many users saying that they will delete the App rather than give up their privacy. Privacy is very important and therefore I believe that we should not let our data be used by big companies like WhatsApp and Facebook.
I have started to look at alternatives to WhatsApp, following the direction of many like-minded people online. There are two Apps that are now fighting for top space in many App stores.
1) Signal
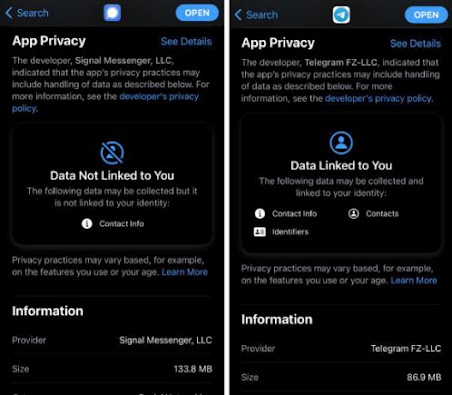
Signal is a new company established in 2014 as a not-for-profit organization. This already sets it apart from WhatsApp which is a company seeking to make money from your data. Signal only stores minimal data about users, including phone numbers and time of account creation, compared to WhatsApp which stores much more.
Signal appears to be winning the battle for top App in many countries. The company even reported that they had experienced a delay in sending verification codes because of the amount of people signing up.
2) Telegram
Telegram has also seen a huge uptake in users since the beginning of this year - some 25 million if reports are to be believed. Telegram was already a popular messaging App before #WhatsAppPrivacyPolicy however has certainly benefited from Whatsapp's policy update.
Like Signal, Telegram is pro-privacy by using encrypted chats and not sharing personal data. However, it is not a private as Signal which suggests why more people on Twitter are supporting that messaging service instead.