Wednesday, September 5, 2018
Can you spot fake accounts? Iran continues to spread disinformation through fake news agencies and social media
Back in January I blogged about how Iran had followed the Chinese in the creation and use of fake social media accounts to further their political agenda. A report by FireEye shows that Iran continues to exploit social medial to promote its political interests and influence other unsuspecting users - fake news appears to be back on the agenda!
The report identifies 'Liberty Front Press' as a fake news agency created by the Iranians to further their political interests, along with a number of associated counterfeit social media accounts. The site promotes Senator Bernie Sanders whilst making anti-trump sentiments. Clearly the Iranians and Russians were not collaborating on this at least! It seems likely the Iranians were worried about Trump's negativity towards the JCPOA and thought Mr Sanders would be the safer option. That has not worked out so well for them.
Other fake news agencies and websites with an Iranian footprint include the 'Real Progressive Front', 'The British Left' and 'Instituto Manquehue'. All these sites go out of their way to state that they are 'completely' or 'genuinely independent', in an attempt to deceive the reader. All have similar political narratives; anti-Saudi, anti-Israeli, pro-Palestinian and pro-Iranian.
It appears the Social Media giants, like Facebook and Twitter, are finally trying to crack down on fake accounts. In the last week, it has emerged that YouTube has blocked 39 channels linked to the Iranian-state-run IRIB network and Facebook has announced the closing of 562 pages all linked to the Iranian regime.The regime, of course, denies all connection to the government.
Social media platforms have the difficult task of distinguishing fake from real accounts - but what identifies an account as suspicious? Whilst the algorithms used by the platforms are unknown, there are probably a number of contributing factors like low levels of original content (copying material from elsewhere), absence of personal photographs in profile pictures, accessing sites through a proxy, inflated number of followers or friends, and promotion of suspect websites. However, this is not easy and there will inevitably be collateral damage; I know a number of people who have had their real accounts shut down for unspecified 'suspicious' behavior. I am worried that banning customers that access platforms through a VPN will have a big impact on Iranian citizens trying to overcome the regime's access restrictions. I hope that in the future they can accurately separate real users who are drawing attention to important human rights issues, from the Iranian, Chinese or Russian (and probably a lot of other countries) actors who are abusing the right of free speech and circulating disinformation.
Labels:
cyber,
Facebook,
fake news,
iran,
iran cyber,
JCPOA,
regime,
social media
Wednesday, April 4, 2018
A cyber-attack on ideas: Mabna behind latest frightening global phising campaign that targets intellectual property, with allegations of state-sponsorship.
An indictment for nine Iranians was unsealed on March 23 2018. They each stand accused of a variety of crimes relating to cyber-attacks conducted on universities, government agencies, and private organisations around the globe. 31 terabytes of data was stolen - that is a lot of data! The nine suspects are all affiliated with Mabna, the group responsible for the HBO hacking (in which Game of Thrones episodes were leaked), which led to the indictment of Mesri for his involvement in the hacking and attempts to extort US$6 million. It has been revealed that the cyber-assault used customized phishing emails that were sent under the disguise of academics at other institutions. The emails contained links to academic papers that directed the victim to a malicious domain masquerading as a university web page, prompting the victim to give away his log-in details.
Among the victims were government agencies and private companies, but the primary target was universities, with around 8000 professors falling victims. So, unlike the targets identified in previous indictments, we now appear to be seeing a diversification of the type and location of the target. Furthermore, the attack was indiscriminate with regards to academic discipline. Whilst the economic value of the data should not be given disregarded (the indictment makes the cost of the stolen research to USE institutions as US$3.4 billion), the financial loss is only one implication. The concept of targeting innovation, ideas and information, acquired through years of research effort, is new and frightening. The attacks demonstrate the need for academic institutions, to improve their cyber-security, both in terms of the awareness and implementation. It is worrying that the attacks reached beyond the usual suspects of the US and Israel; universities in 22 different counties, including many in Europe, and also China, were victims. Among the non-academic targets was the Unite Nations Children's Fund, demonstrating the callous and indiscriminate way in which the Iranian cyber machine selects victims.
Whilst considered innocent until proven guilty in a court of law, presumably investigators must be pretty convinced of guilt to name these individuals in the indictment. These men will join those previously indicted by the FBI for cyber-criminals, in not being able to leave Iran without fear of arrest. This limitation of freedom will surely deter some of those considering a 'career' in hacking, and slow recruitment to the Iranian cyber-army.
Who is backing Mabna? The indictment reveals that spear-phising email attacks were then conducted on behalf of the Islamic Revolutionary Guard Corps (IRGC) of Iran. But were there other governmental bodies involved? This is a persistent question which resurfaces with each attack. Given their close association, it seems likely that there is some level of co-ordination between the IRGC and other government offices, like those within the Iranian Ministry of Foreign Affairs, when planning the cyber-attacks. Will this public condemnation deter Iran form undertaking further attacks on university, or will the stat simply distance themselves form cyber criminals?
Among the victims were government agencies and private companies, but the primary target was universities, with around 8000 professors falling victims. So, unlike the targets identified in previous indictments, we now appear to be seeing a diversification of the type and location of the target. Furthermore, the attack was indiscriminate with regards to academic discipline. Whilst the economic value of the data should not be given disregarded (the indictment makes the cost of the stolen research to USE institutions as US$3.4 billion), the financial loss is only one implication. The concept of targeting innovation, ideas and information, acquired through years of research effort, is new and frightening. The attacks demonstrate the need for academic institutions, to improve their cyber-security, both in terms of the awareness and implementation. It is worrying that the attacks reached beyond the usual suspects of the US and Israel; universities in 22 different counties, including many in Europe, and also China, were victims. Among the non-academic targets was the Unite Nations Children's Fund, demonstrating the callous and indiscriminate way in which the Iranian cyber machine selects victims.
Whilst considered innocent until proven guilty in a court of law, presumably investigators must be pretty convinced of guilt to name these individuals in the indictment. These men will join those previously indicted by the FBI for cyber-criminals, in not being able to leave Iran without fear of arrest. This limitation of freedom will surely deter some of those considering a 'career' in hacking, and slow recruitment to the Iranian cyber-army.
Who is backing Mabna? The indictment reveals that spear-phising email attacks were then conducted on behalf of the Islamic Revolutionary Guard Corps (IRGC) of Iran. But were there other governmental bodies involved? This is a persistent question which resurfaces with each attack. Given their close association, it seems likely that there is some level of co-ordination between the IRGC and other government offices, like those within the Iranian Ministry of Foreign Affairs, when planning the cyber-attacks. Will this public condemnation deter Iran form undertaking further attacks on university, or will the stat simply distance themselves form cyber criminals?
Friday, March 16, 2018
Are large scale human casualties inevitable in state sponsored cyber war?
The attack on the Saudi Petrochemical Company in August represents a terrifying escalation in cyber wars. The machinery was the primary target, but human casualties would have been almost certain. Whether human death was the intention or just an accepted consequence is not known, but doesn't really matter - the attackers would have been aware that large scale casualties were likely and still went ahead with the attack.
Worryingly, the complexity of the malware indicates a level of resourcing that suggests the attacks were state sponsored. Although the culprit has not yet been confirmed by investigators, the open hostility between Iran and Saudi Arabia and the step change in the intensity of hostile cyber activity, make the Iranians an obvious candidate.
The malware (which has been named Trisis) compromised machinery that is common in other nuclear and oil companies throughout the world - this demonstrates the potentially global destruction that can be rapidly released by a single well planned cyber attack.
Where do we go from here? For now we can be thankful that the attacked failed and was detected. But if the bug that caused the malware to fail has been fixed, are all industrial systems sitting on a ticking time bomb with human casualties inevitable collateral damage? Attribution will be difficult, but if a government such as Iran are behind these attacks, then their consideration towards human life is very worrying. These are scary times.
Labels:
cyber warfare,
hackers,
iran,
iranian state,
Saudi Arabia
Tuesday, January 9, 2018
Mesri remains silent; where next for exposed Iranian hackers?
Just over a month ago, the US announced the indictment of Behzad Mesri (Skote Vahshat) who has been indicted by the FBI for computer fraud, extortion, and identity theft.
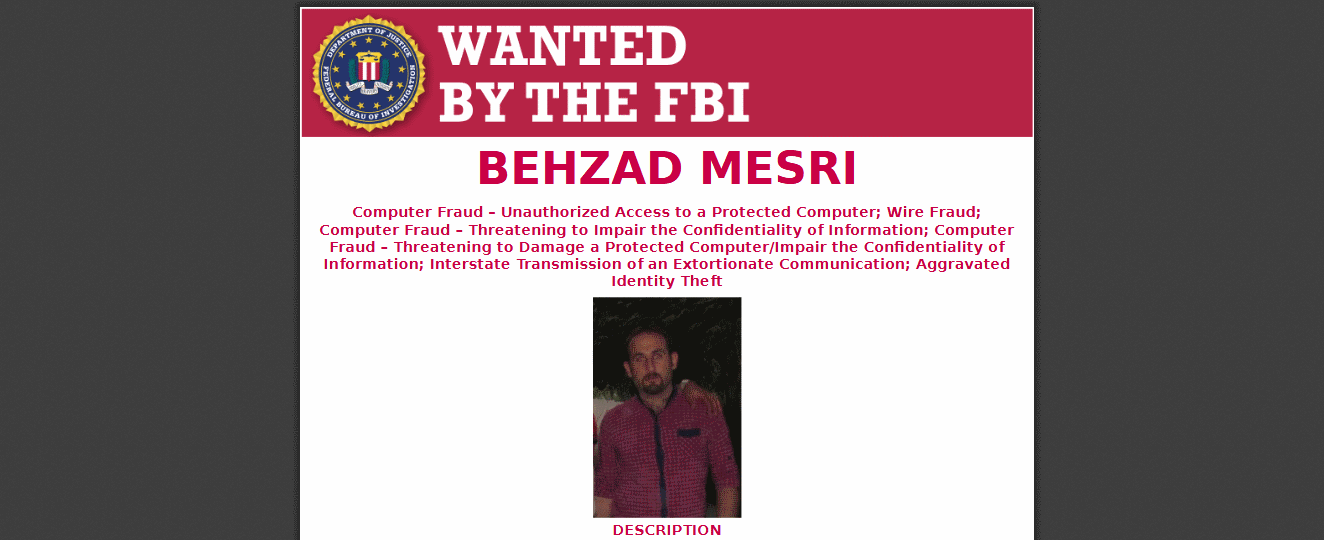
It seems that Mesri is a member of Turk Black Hat Iranian hacking group, which is responsible for defacing hundreds of websites, and most famously, the hacking of HBO's computer servers. As expected, we have heard nothing from Mesri himself.
Silence, in such cases, means that the accused is unable to justify their actions; was he doing it for someone else? Was it for money or ideology? The fate of exposed hackers in Iran is unlikely to be good.
As noted in the US indictment, Mesri will be unable to travel abroad and presumably for this reason, there will not be so many opportunities for employment in the future. Whether staying silent is Meri's own decision, or whether he was obeying orders form higher up the command chain, is not known. Although the cybersecurity consulting and intelligence company Clearsky have recently reported evidence linking Mesri to the Iranian hacking group Charming Kitten, it is still unclear if this group and other Iranian hacking groups are working for the Iranian government.

It seems that Mesri is a member of Turk Black Hat Iranian hacking group, which is responsible for defacing hundreds of websites, and most famously, the hacking of HBO's computer servers. As expected, we have heard nothing from Mesri himself.
Silence, in such cases, means that the accused is unable to justify their actions; was he doing it for someone else? Was it for money or ideology? The fate of exposed hackers in Iran is unlikely to be good.
As noted in the US indictment, Mesri will be unable to travel abroad and presumably for this reason, there will not be so many opportunities for employment in the future. Whether staying silent is Meri's own decision, or whether he was obeying orders form higher up the command chain, is not known. Although the cybersecurity consulting and intelligence company Clearsky have recently reported evidence linking Mesri to the Iranian hacking group Charming Kitten, it is still unclear if this group and other Iranian hacking groups are working for the Iranian government.
Tuesday, January 2, 2018
Iranian hackers join Chinese in the use of fake social media profiles:
In December, reports were published that the German intelligence services have uncovered use of fake social media profiles by Chinese intelligence. However, it is not just the Chinese that use this type of deception; Clearsky have reported that Iranian cyber criminals are doing the same.
The report provides evidence demonstrating that the Iranian cyber group Charming Kitten have created LinkedIn company pages and profiles for a fake news-agency called 'British News', in an attempt to authenticate their British News website, which has been set up to infect targeted visitors. The hacking group also used false Facebook and Twitter profiles to 'verify' fake personas when emailing targets. These more innovative methods were being used alongside more 'well-known' techniques, such as spear phishing.

The report provides evidence demonstrating that the Iranian cyber group Charming Kitten have created LinkedIn company pages and profiles for a fake news-agency called 'British News', in an attempt to authenticate their British News website, which has been set up to infect targeted visitors. The hacking group also used false Facebook and Twitter profiles to 'verify' fake personas when emailing targets. These more innovative methods were being used alongside more 'well-known' techniques, such as spear phishing.

Labels:
British,
Chinese,
fake news,
fake persona,
German,
hacked,
iran,
spear-phishing
Subscribe to:
Posts (Atom)
-
Web browsers generally allow users to send a "Do Not Track" signal that informs advertisers that the users do not want to be ...
-
Ashiyane Security Group (officially Ashiyane Information and Communication Technology Company) is one of the oldest cyber security group...
-
The Heartbleed bug is a serious vulnerability in the popular OpenSSL cryptographic software library and this weakness allows stealing t...
-
Head of Iran Cyber Police (FATA) General Seyed Kamal Hadianfar asked for collective efforts by all world states to prevent the spread of...
-
Funeral reception of Mohammad Hussein Tajik News of the assassination of an Iranian Cyber manager has recently been released. Mohammad H...
-
Since my last post in October, there has been no confirmation of which group was behind the cyber-attack on Westminster, or the role of the ...
-
Duqu 2.0: ‘Almost Invisible’ Cyber Espionage Tool Targeted Russian Co., Linked to Iran Nuclear TalksA Russian cyber security company says that it has discovered a highly-technical, “almost invisible” cyber espionage tool that t...
-
Are Iranian hackers involved in using the " Mamba " ransomware (or possibly be behind the ransomware)? It seems unclear but an...








